how to log a data breach
We know we must inform affected individuals without undue delay. Check data breach websites.

Data Breach Response Times Trends And Tips
Some online services allow you to view what devices have recently used your login details and any recent transactions.

. A data breach is a security violation or incident that leads to the theft of sensitive or critical data or its exposure to an unauthorized party. Many data breaches will affect your passwords even if it also affects other data. We have a process to inform affected individuals about a breach when their rights and freedoms are at high risk.
Follow These 8 Steps After a Data Breach. The websites will tell you if your email and associated passwords were part of any known data breaches. Assigned Data Beach Number 26659 - Beacon Hospice LLC.
A personal data breach is. Assemble a team of experts to conduct a comprehensive breach response. However these actions remain fairly consistent year over year with slight deviations depending on technology.
The first thing to do. Make sure the new password is secure and has nothing to do with the prior one. Below find copies of data breach notification letters sent to consumers impacted by a data breach.
Make it harder for hackers to log in to your accounts by creating two ways to gain access. You should act on this type of breach as soon as possible. The log should describe the incident itself the cause repercussions risk of future damage affected data and measures taken to mitigate the risks to further damage.
A data breach occurs when a companys or individuals stored data is accessed or open to access by unauthorized parties. Cybercriminals can steal a lot of sensitive information during a data breach including personally identifiable information PII personal health information PHI company trade. Analyzing logs is the primary way of doing forensics and properly managed logs can also be used as evidence in a court of law for prosecution purposes.
Ask your forensics experts and law enforcement when it is reasonable to resume regular operations. We know who is the relevant supervisory authority for our. The log should describe the incident itself the cause repercussions risk of future damage affected data and measures taken to mitigate the risks to further damage.
Responding to a personal data breach We have in place a process to assess the likely risk to individuals as a result of a breach. To prepare for a data breach event policies actions and tools can be put in place to lay out a plan for detecting and containing an event while minimizing overall exposure in the first. Ad Implement a complete Identity and Access Management strategy rooted in Governance.
Implement tools services and policies. The DBIR 2020 lists nine core clusters of incidence classification patterns which account for about 88 of data breaches. Confirm your account details which will go straight to the hacker.
Download the Strategic Business Leaders Framework to learn best practices. Data breaches are extremely common. Review logs to determine who had access to the data at the time of the breach.
Freeze Your Credit. They are the common ways in which data breach incidences were occurring in 2020. Teachers should learn more about cybersecurity including relevant risks and what steps work best against them.
Next they should aim to minimize the data they collect and share. These incidents can be intentional such as a database hack or accidental such as an employee emailing confidential files to the wrong recipient. 15 hours agoFor the third straight year the number of data breaches is rising.
When to report a data breach under GDPR. The exact steps to take depend on the nature of the breach and the structure of your business. Be sure to log into the affected accounts to change your password.
Data loss a mystery for many businesses. This means creating a. Millions at risk of data breach through Log4j flaw.
The Breach Notification Law MGL. Current Data Breach Methods. 3 requires that a person or agency including public and private entities that maintains stores owns or licenses data that includes personal information about a resident of the Commonwealth shall provide notice as soon as practicable and without unreasonable delay when such person or agency 1 knows or has reason to know.
Professional development is critical in making opportunities from challenges and cybersecurity is no different. A data breach is a security violation or incident that leads to the theft of sensitive or critical data or its exposure to an unauthorized party. Contact IDCare on 1800 595 160 or use their.
PDF 1741 KB Assigned Data Beach Number 26676 - Global Wireless Solutions PDF 54615 KB Assigned Data Beach Number 26678 - Varsity Tutors LLC PDF 31738 KB. Confirm the breach has happened but be cautious of emails Find out what sensitive data was stolen and is available to hackers. Ad Download Top 50 Security Threats to learn more.
Refer to the Office of the Australian Information Commission Respond to a data breach page for more steps you can take. Meaning cybercriminals can gain access to your information through an organisation website or other places you have previously inputted your data. For the third straight year the number of data breaches is rising.
Fyp fnaf roblox viral fnafsecuritybreach foryou. If your Social Security number or financial information was part of a data breach freezing your credit will restrict access to. Manage risk at scale with Identity Security.
Sometimes a data breach involves financial information including credit card numbers or bank account information. Data Breach Incident Log Template. Ad Learn how to optimize a compliant and defensible incident response plan.
An email data breach can happen when there are security issues with an email. Set up a fraud alert or credit freeze. Learn some of the most common cyberthreats being used by hackers today.
Your first priority at this point in time is to isolate the affected system s to prevent further damage until your forensic investigator can walk you through the more complex and long-term containment. According to the GDPR legislation an organization must report a data breach to a data protection authority DPA also known as a supervisory authority. You can usually also log out those devices from these settings.
Secure your log-ins passwords and PINS and add 2FAMFA. A personal data breach is. A data breach is when your personal data is accessed copied or changed by someone without your permission.
Dont wipe and re-install your systems yet Do follow your incident response plan. Mobilize your breach response team right away to prevent additional data loss. To make a secure.
A data breach occurs when cybercriminals steal information from an organizations database without permission from the owner or administrator. 2 days agoTeachers can do a lot to protect student data sets. Most data breaches involve hacked email accounts and stolen bank information.
Just click here to log in And now theyve. One of the best ways to check if you have been hacked is to enter your email into a number of data breach websites that track breaches and verify them as genuine. First you have to record the date and time you identified the data breach.
Hackers breaking into a storage server to steal financial information from bank clients or a health care employee losing their laptop that contains patients digital records are just two examples of how data breaches can occur. GDPR requires all firms to keep a log of any and all breaches even the smallest incidents should be recorded.

Flyers Saint Eu Project Cyber Security Cyber Threat Intelligence Cyber Threat

Known Data Breaches Heavy Fines Ahead Data Breach World Data Big Data

How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies

How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies

How To Avoid Getting Sued For A Data Breach Insureon

Pin On Information Security Cyber Tip Posters

Impact Of Data Breach On The Legal Industry Infographic Data Breach Productivity Infographic Social Media Infographic

Onelogin Businesses Vulnerable To Data Breaches By Ex Employees Data Breach Data Vulnerability

Login With Facebook Data Hijacked By Javascript Trackers Techcrunch Data Marketing Insights Tracker
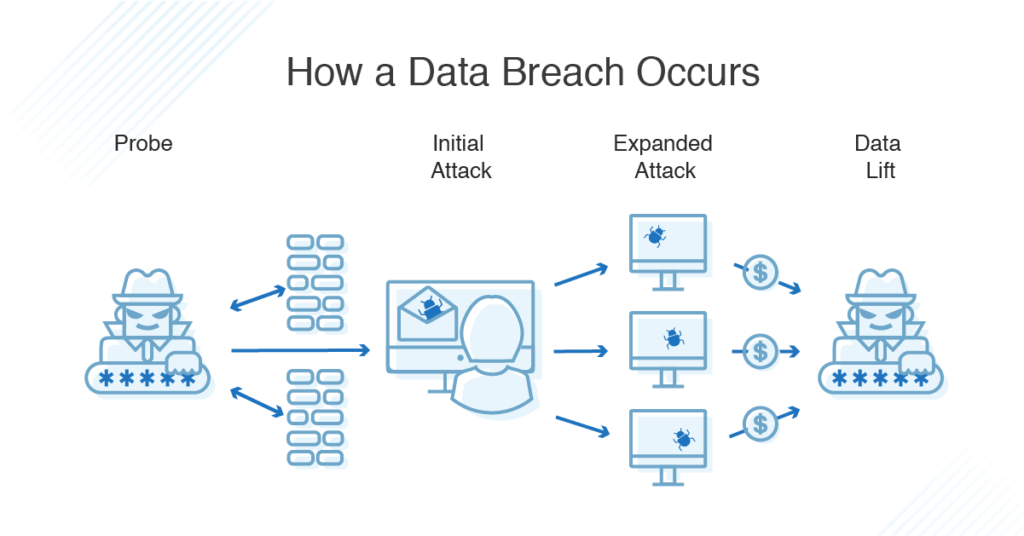
What Is A Data Breach Definition Types Dnsstuff

Handling Data Breaches In Your Business Privacy Policies

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

Common Data Breach Causes Cyber Security Awareness Infographic Marketing Data Breach
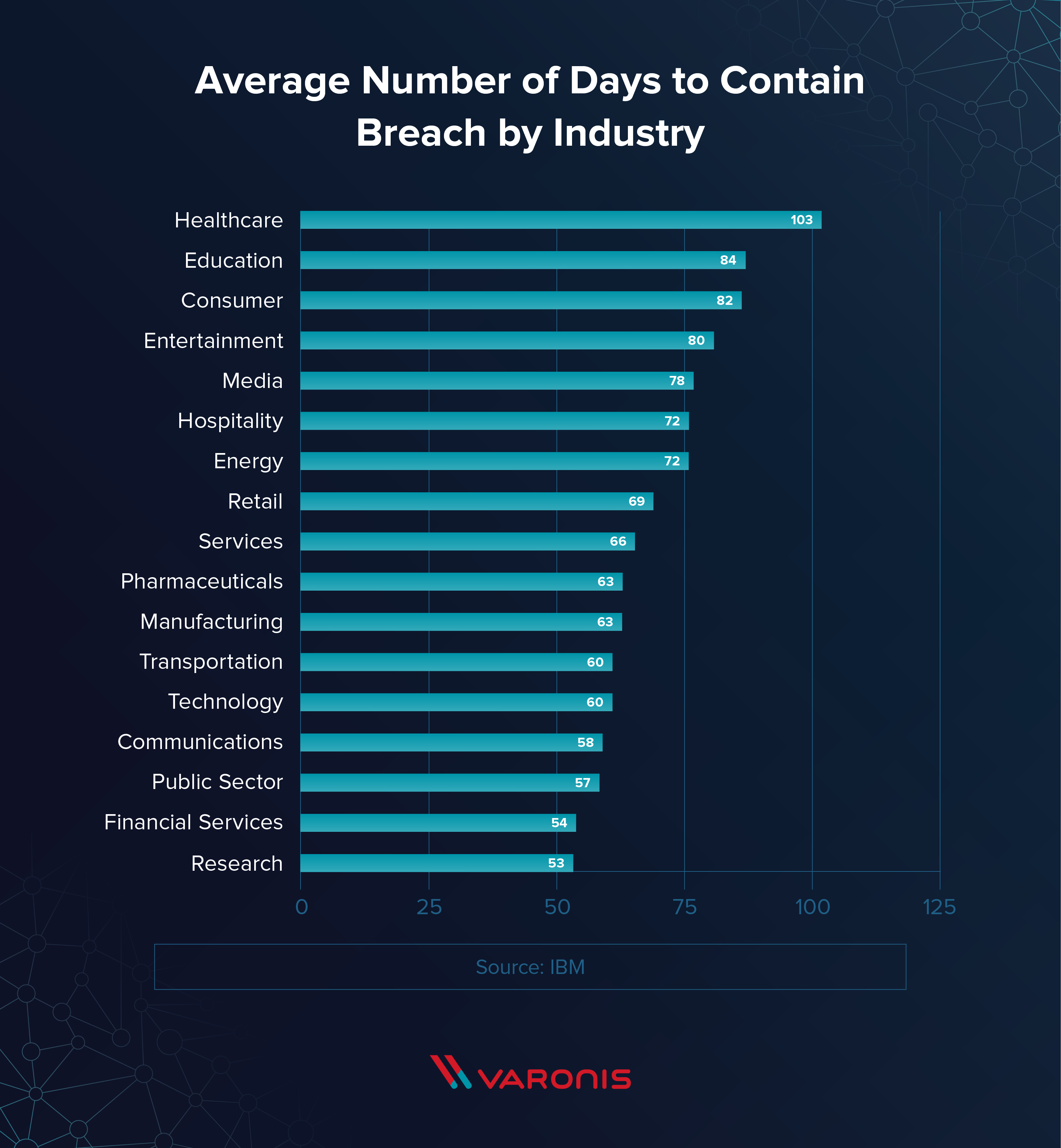
Data Breach Response Times Trends And Tips

Data Breach Infographic Data Breach Shocking Facts Infographic

How To Deal With A Data Breach Of Your Personal Info Privacy Policies

Data Breaches In The Financial Service Industry Rise In 2016 Fintech Security Data Breach Infographic Cyber Security